gNMIc is a gNMI CLI client that provides full support for gNMI RPCs. Nokia developed the gNMIc and donated it to the open-source community, OpenConfig. gNMIc is widely used by the open-source community, developers, and networking vendors. To understand how gNMIc works, let’s introduce gNMI. What is gNMI? gNMI (gRPC… Read more »
[Disclaimer: This “story” was written with the help of ChatGPT by feeding it with course material covering the five key areas of network management.] In the ever-evolving world of network management, an intrepid network engineer embarks on a quest to transform chaos into order. Armed with determination and a vision,… Read more »
Note: This article has been initially appeared on LinkedIn. I have been asked this question a lot lately by students who are confused about the terms. Perhaps, because the IT industry uses the terms interchangeably in many ways. I have been teaching Network Design for about 17 years and for… Read more »
Introduction Alpine Linux is a Linux distribution designed for security, simplicity and resource efficiency. It is also small (around 4MB w/o GUI) and is designed to run directly from RAM. Alpine Linux is a good choice for creating Docker containers or to deploy applications in the cloud. Alpine Linux does… Read more »
Introduction The market is flooded with many home automation products that includes environmental sensors, smart light bulbs, smart switches and others. The technologies that connect these devices include Bluetooth, ZigBee, Z-wave, or Wi-Fi. The common pattern of using these products is to use a mobile app to access the sensors…. Read more »
Batfish is an open source network configuration validation and verification software. The article reviews and demonstrates some major features of the software by using it to analyze configuration files of three small networks.
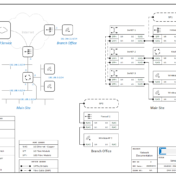
Professionals in any discipline need a common language to convey messages and exchange ideas. This language may be in verbal, written, and/or visual form. Engineers, for example, use technical drawings to describe a product or a component. The purpose of these drawings is to convey all information necessary to fully… Read more »
Keep it simple, stupid (KISS) is a design principle that requires a system’s design to be as simple as possible. Complex design may be expensive to build and maintain. Also, unnecessary features or components increase the potential for failures. From a management perspective, network designs should be simple enough for… Read more »
Scalability is the measure of a system’s ability to increase or decrease in performance in response to changes in demands. For networks, this means change in the number of users, number of end nodes, the amount of bandwidth, or the demand on any service provided by the network. Networks need… Read more »
Redundancy is a primary tool to create resilience in communications networks. It eliminates the single point of failure by relying on the probability that it is rare that two network components fail at the same time. Redundancy can be classified into [Lidwell]: Diverse redundancy Diverse redundancy uses multiple components of… Read more »